Exam Tips
AWS CLI
- Least Privilege
- Always give your users, the minimum amount of access required to do the job.
- Use Groups
- Create IAM policy groups and assign your users to the groups. Group permissions are assigned using IAM policy documents.
- Secret access key
- You only see this ones. If you lose it you can delete the access key and secret access key and regenerate them. You need to run AWS configure again.
- Don’t share key pairs
- Each developer should have their own access Key ID and secret access Key. Just like passwords, they should not be shared.
- Supports Linux, Windows, macOS
- You can install CLI on your Mac, Linux, or Windows PC. You can also use it on EC2 instances.
AWS CLI Pagination
- If you see errors like “ timed out”, or errors related to too many results being returned.
- Adjust the pagination of CLI results to avoid errors generated by too many results.
- aws S3 api list-objects - - bucket my-bucket - - page-size 100.
- The CLI still retrieves the full list, but performs a large number of API calls in the background and retrieves a smaller number of items with each call.
AWS Roles
- Roles are a preferred option from security perspective.
- Roles allow us to provide access without the use of access key ID and secure access keys.
- Policies, control roles permissions.
- We can update a policy attached to a role and it will take immediate effect.
- You can attach and detach roles running EC2 instance, without having to stop or terminate the instance.
AWS RDS
- RDS database types
- SQL Server, Oracle, mySQL, PostgresSQL, Maria, DB, and Amazon Aurora.
- RDS is for 0LTP workloads
- Great for processing. Lots of small transactions, like customer orders, banking, transactions, payments and booking systems.
- Not suitable for OLAP.
- Use red shift for the data warehousing and OLAP tasks, like analysing large amounts of data, reporting, and sales forecasting.
AWS SECRETS MANAGER
- Centrally manage secrets used to access resources inside and outside AWS.
- Rotate secrets without code deployment.
- Secure secrets with control of fine, grain permissions and encryption with AWS KMS.
- Secret types
- RDS database
- Red shift cluster
- Document DB database
- Other API keys
AWS EC2 IMAGE BUILDER
- EC2 image builder automates the process of creating and maintaining AMI and container images.
- It is a 4 step process
- Select a base OS image.
- Customised by adding software.
- Test and distribute to your chosen region.
- Terminology
- Image pipeline
- Settings and process.
- Image recipe
- Image and build components.
- Build components
- The software that you want to include.
Version control with lambda
- $Latest is always the last version of Code. You want to upload to lambda.
- Versioning and aliases
- Use lambda, versioning and Alias is to point your applications to a specific version if you don’t want to use $Latest.
- Example ARN
- ARN of lambda:$Latest
- arm of lambda:prod
- If your application uses an alias instead of $Latest, remember that it will not automatically use the new code when you upload it.
Lambda Concurrent executions limit
- 1000 concurrent executions per second.
- If you hit the limit, you will see invocation being rejected – 429 HTTP status code.
- The remedy is to get the limit raised by AWS support.
- Reserve concurrency guarantees, a certain number of concurrent executions are always available to a critical function.
Lambda and VPC access
- We can have lambda to access VPC resources
- It is possible to enable lambda to access resources that are inside a private VPC.
- VPC config information
- VPC ID, private Subnet ID, security group ID.
- Network access
- Lambda creates elastic network interfaces using IP’s from the private Subnets. The security group allows your function to access the resources in the VPC.
- Server-less architectures are event driven and asynchronous
- An event or message might trigger an action, but no response is expected or required.
- Think of AWS SERVICES as building blocks that can be Integrated together to create an application.
- Event driven architectures are loosely, coupled services like SQS allows you to queue messages.
- Event bridge helps you to handle events and route them to application components.
- Flexibility and scalability
- Services and components operate and scale independently of each other.
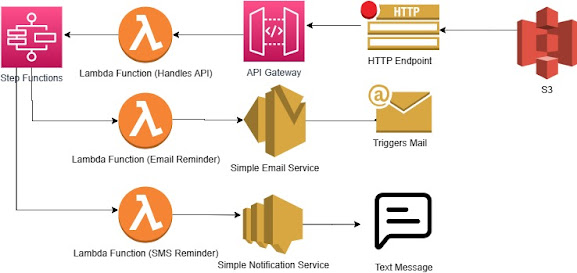
AWS Step functions
- Great way to visualize your server-less application.
- Step functions automatically trigger and track each step.
- The output of one step is often the input of next step.
- Step functions log the state of each step, so if something goes wrong you can track what went wrong, and where.
- There are two types of step function workflows.
- Standard workflows
- Long running up to 1 year
- At most once
- Non-Idempotent
- Express workflows
- Short lived up to 5 minutes
- At least once
- Idempotent
- Synchronous express workflows
- The workflow must complete before the Next step begins example confirm successful payment before sending an order.
- Asynchronous express workflows
- Other tasks are not dependent on the completion of the workflow example a messaging system.
Comments
Post a Comment