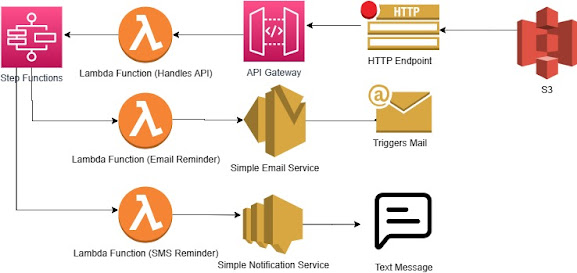
Ephemeral vs Persistent Data Storage Patterns
Storage patterns available with lambda Ephemeral Storage Patterns Persistent Storage Patterns Lambda is stateless Functions are stateless, meaning that you can’t permanently store any data in the function(Example, session data, customer data, etc). Lambda is Ephemeral Not used for applications that need to run for longer than 15 minutes(Example, a database application or a web server That needs to stay up and running). Persisting data To persist data, The function must interact with a data store(Example save it to S3, EFS, Or Dynamo DB).